| Cryptosystem ME6 — User Manual |

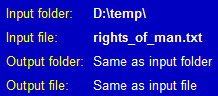
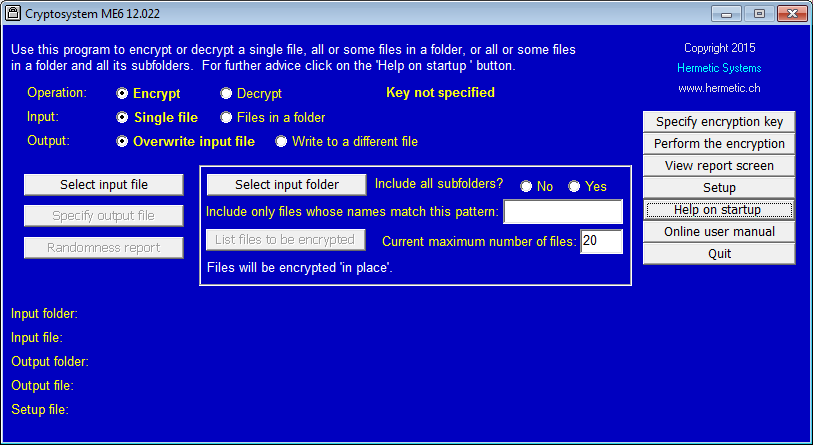
 You can encrypt a single file so that either (a) the output file is different from the input file (in which case you must first specify a location and a name for the output file) or (b) the output file has the same location and name as the input file (in which case the input — plaintext — file is replaced by the output — ciphertext — file). The locations and names of the input and (if different) the output file are displayed after you have specified them.
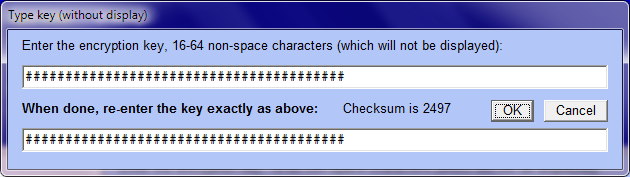
You can encrypt a single file so that either (a) the output file is different from the input file (in which case you must first specify a location and a name for the output file) or (b) the output file has the same location and name as the input file (in which case the input — plaintext — file is replaced by the output — ciphertext — file). The locations and names of the input and (if different) the output file are displayed after you have specified them. Before encrypting you must specify an encryption key. There are several ways to do this, but the easiest is to enter a key via the keyboard. For example:
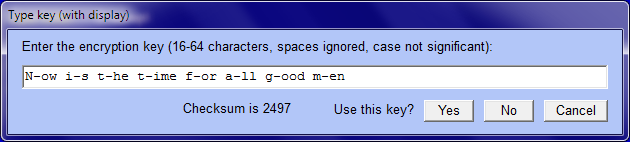
Before encrypting you must specify an encryption key. There are several ways to do this, but the easiest is to enter a key via the keyboard. For example:
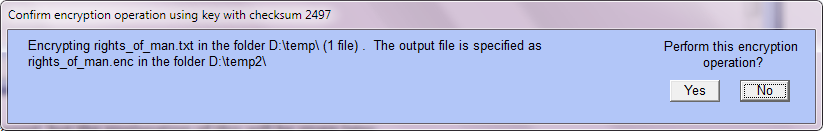
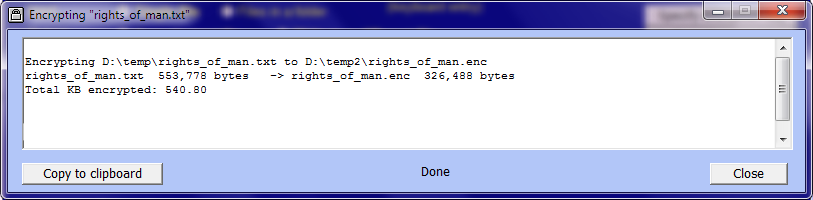
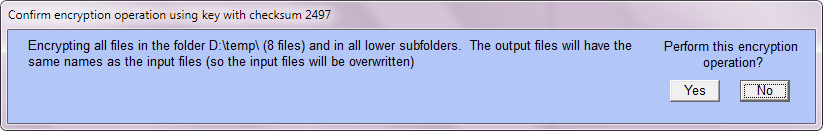
When encrypting a single file 'in place', the confirmation window and the report window are very similar to the case of when the output file is different.

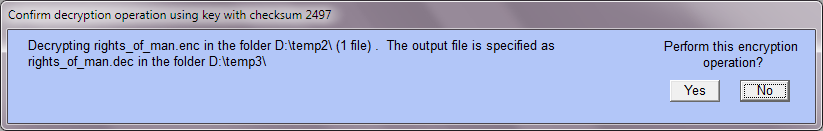
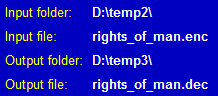 Decryption is very similar (select 'Decrypt'). As when encrypting, you can decrypt a file so that either (a) the output file is different from the input file (in which case you must first specify a location and a name for the output file) or (b) the output file has the same location and name as the input file (in which case the input — ciphertext — file is replaced by the output — plaintext — file).
Decryption is very similar (select 'Decrypt'). As when encrypting, you can decrypt a file so that either (a) the output file is different from the input file (in which case you must first specify a location and a name for the output file) or (b) the output file has the same location and name as the input file (in which case the input — ciphertext — file is replaced by the output — plaintext — file).
To be safe, however, it's best simply to disable any anti-malware software while running Cryptosystem ME6.
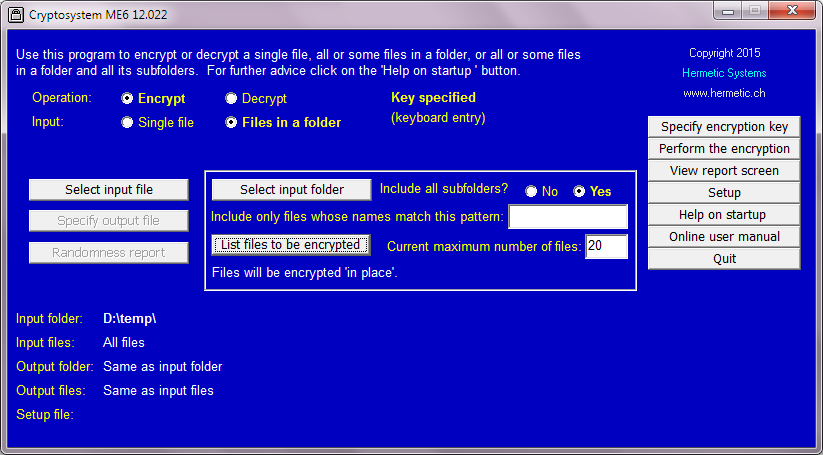
When 'Files in a folder' is selected, the controls within the frame are activated (they are inactive when 'Single file' is selected). The operation can be modifed either (a) by specifying whether to include subfolders (if any) of the folder and (b) by specifying whether to include only files whose names match a given pattern (as explained below).
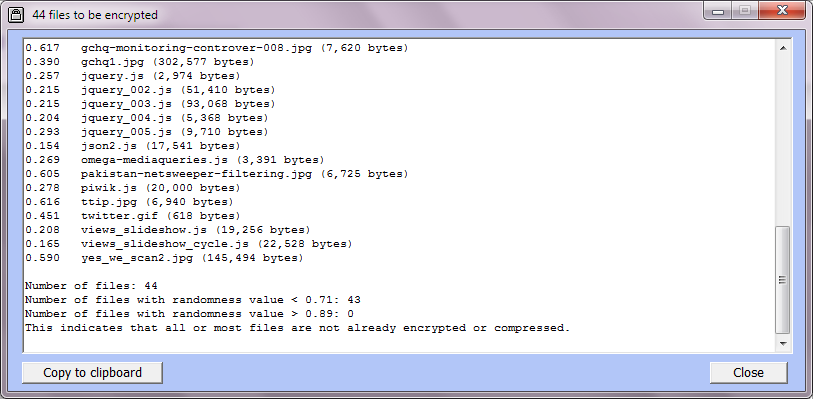
Here is an illustration of encrypting eight files in a folder \temp plus (since two of them are 'htm' files) two subfolders (holding images and other files associated with the two 'htm' files), for a total of 44 files, using the same key as above. Here is the initial setup. Note that 'Include all subfolders?' is set to 'Yes', and the textbox for a file pattern is empty (thus all files are included).
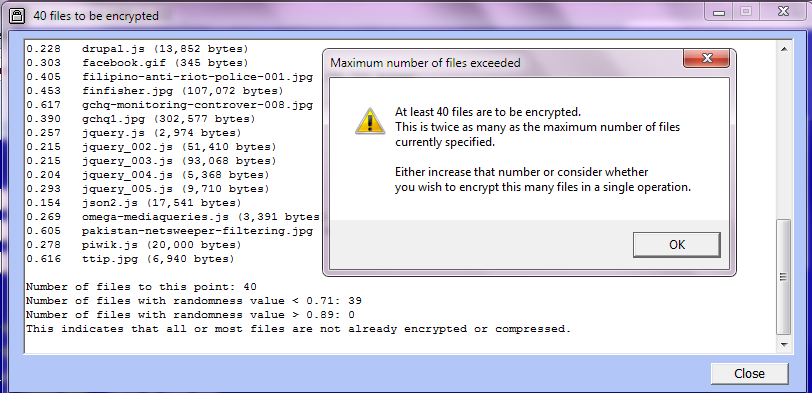
The current maximum number of files acts as a check on whether you are attempting to encrypt more files than you thought you were. In this case we simply set the maximum number to a larger number. Setting it to 50 and re-listing gives:
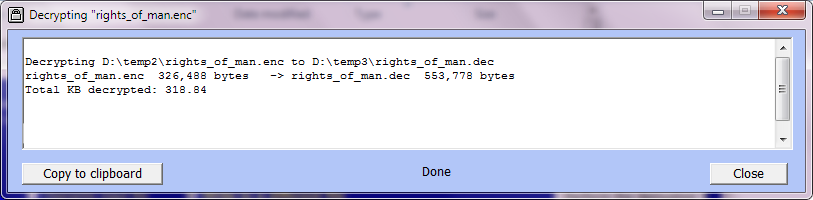
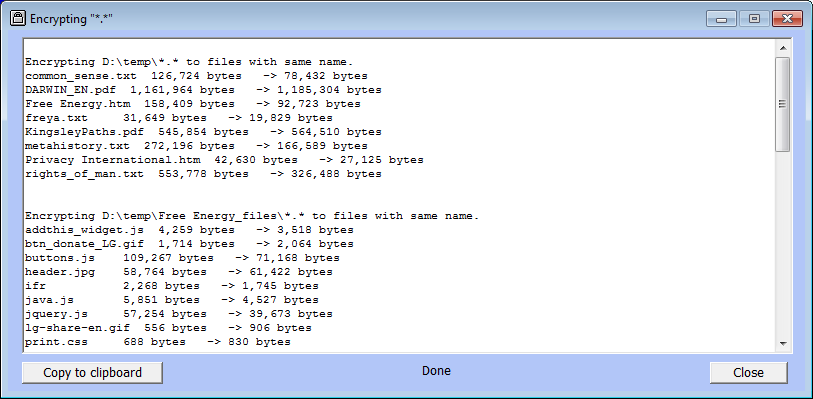
At the end of the operation the report window looks like this:
As with encryption, it is highly recommended to list the files to be decrypted. In this case we obtain:
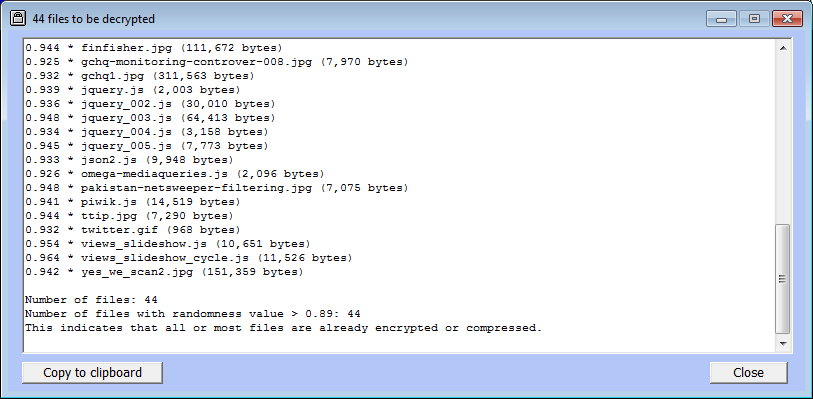
Note that all the randomness values are greater than 0.9, showing that the files are encrypted. Noting the randomness values of files to be decrypted protects against an accidental attempt to decrypt files which are not encrypted.
The confirmation window for decryption, and the report window, are very similar to those for encryption as shown above.
When decrypting, you have to be careful to specify the same file pattern to ensure that only the encrypted files will be decrypted. But if you forget, and attempt to decrypt all files, then listing the files before decryption will reveal that there are unencrypted files (those with low randomness value).
A randomness value near zero means "very non-random" and a larger randomness value indicates a greater degree of randomness. Randomness values may range from close to zero up to nearly 1 (seldom above 0.975), with 0.9 and above indicating a high degree of randomness. Compressed files (such as 'zip' files often have a randomness value of about 0.8.
Randomness values are given in any listing of files to be encrypted or decrypted. A files must have at least 256 bytes in order to have a randomness measure. Files whose randomness is at least 0.9 are marked (in the listing) by an asterisk.
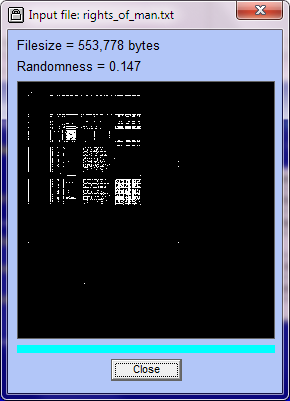
It is also possible in Cryptosystem ME6 to obtain a graphical display of randomness. This is done by taking each successive pair of bytes and treating them as an x-coordinate and a y-coordinate, and (with a black background) placing a white pixel at that point.
After selecting a single file for encryption, clicking on 'Randomness report' will give such a graphical display (such as below at left). If you then encrypt that file to a different output file, the randomness report will be like the image at right:
 |
 |
You can inspect the randomness of any file by specifying it as a single file then clicking on 'Randomness report'. In particular, if you are unsure as to whether a file you wish to encrypt is or is not already encrypted then specify it as the file to be encrypted and click on 'Randomness Report'. If the graphical display shows a randomness value > 0.9 (like the image at right) then the file is encrypted. Conversely, if you are unsure as to whether a file you wish to decrypt is in fact encrypted then specify it as the file to be decrypted and get a randomness report (a randomness value of < 0.8 means the file is not encrypted).
When you encrypt a single file 'in place', after the encryption the output file has the same location and name as the input file, and clicking on 'Randomness report' will show that the file is encrypted (the display will be the same as what you would get by encrypting the input file to a different output file).
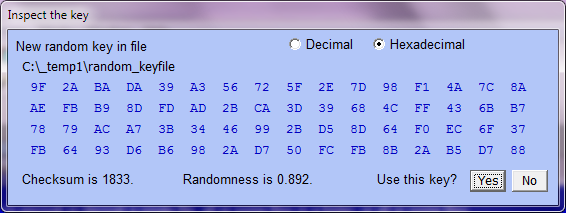
 As noted above, there are several ways to enter an encryption key, the easiest way being via the keyboard. Another way is to select a file — most files will do. Cryptosystem ME6 will then extract 64 bytes from this file to use as a 64-byte key (which you can inspect). The advantage of this method for specifying a key is that you only have to remember the location and name of the file. The disadvantage is that if you forget that, or you accidentally delete the file, then you no longer have the key, so can't decrypt files which were encrypted using that key.
As noted above, there are several ways to enter an encryption key, the easiest way being via the keyboard. Another way is to select a file — most files will do. Cryptosystem ME6 will then extract 64 bytes from this file to use as a 64-byte key (which you can inspect). The advantage of this method for specifying a key is that you only have to remember the location and name of the file. The disadvantage is that if you forget that, or you accidentally delete the file, then you no longer have the key, so can't decrypt files which were encrypted using that key.The most secure key that you can use is a 64-byte random keyfile, since there are 25664 such keys possible (more than 10154). After clicking on 'Create random keyfile' the program asks for the location and name of the file to be created, then the byte values are obtained from your random mouse movements.
You can then inspect the bytes in the keyfile.
 The setup consists of the settings (other than the key, if specified) just prior to performing an encryption or decryption operation. If you usually perform an operation on a particular file or folder then it is convenient to save the setup for the next run (in which case it will be loaded when you run the program again). You can also save the setup to a file and re-load it as needed.
The setup consists of the settings (other than the key, if specified) just prior to performing an encryption or decryption operation. If you usually perform an operation on a particular file or folder then it is convenient to save the setup for the next run (in which case it will be loaded when you run the program again). You can also save the setup to a file and re-load it as needed.Saving the setup, however, involves a security risk, since a setup file contains information about which file or folder was used in an operation. In the case of the setup-for-next-run file you are given the option, when quitting, of wiping (by overwriting) this file.
| Cryptosystem ME6 |