|
The standard claim of apologists for mass surveillence is: "If you have nothing to hide then you have nothing to worry about." There are several answers to this — apart from the obvious facts that no-one likes being watched (without their permission) and that everyone has something to hide (such as the details of their bank accounts).
Firstly, if you work with proprietary or confidential information, such as business plans, software code, financial statements, etc., then you may very well wish to hide this from others who might make use of it to your disadvantage (and if you work for a company which owns this information then your failure to hide it from your company's competitors may lead to your dismissal).
Secondly, as Edward Snowden said in an interview with the Guardian: "... you don't have to have done anything wrong. You simply have to eventually fall under suspicion from somebody even by a wrong [phone] call. And then they can use this [PRISM] system to go back in time and scrutinize every decision you've ever made, every friend you've ever discussed something with. And attack you on that basis to sort of derive suspicion from an innocent life and paint anyone in the context of a wrongdoer."
Despite public outrage at the development of a total surveillance state, NSA programs such as PRISM are continuing. You can, however, do something to prevent the NSA from reading your confidential email messages. You could use public key cryptography in some form. This requires the creation of a 'private' key and a 'public' key, and anyone who wishes to send you an encrypted message has to know your public key (and you then decrypt the message using your private key). This is fine, but it's complicated and requires considerable attention to detail, so is really only suitable for the tech-savvy. There is an easier way to keep your messages and data confidential.
Email Encryption End-to-End allows you to create an encrypted file containing both a text message and a separate file of any type (such as a graphics image or an Excel file). You can then attach this encrypted file to an ordinary email message, send it, and the recipient can recover your text message and the extra file using the same software. Your message and file remain encrypted from start to finish, frustrating any attempt by unauthorized agents to read them.
Suppose your company wishes to send you somewhere to negotiate a business deal with some other company. They will want to know the details of the deal you make with that company as soon as you have concluded the negotiation, so you are to write it up on your laptop. Suppose also that an Excel file with confidential data is to accompany this report. But your company's competitors would dearly like to know the details of the deal you make, so you are instructed to send this information in encrypted form. Before leaving, you are given a phrase to use as the encryption key. After several days negotiation you reach a deal.
Here's how you send your report and the Excel file:
Without being online, you run Email Encryption End-to-End (EEE) and you:
- compose your report in the textbox (up to 60 Kb) and mention what's in the Excel file
- tell EEE the location of the Excel file
- tell EEE the location and name of a file in which it will write its output — the 'ciphertext file (which should have a 'zip' file extension)
- enter the phrase which your company gave you to use as the encryption key, and then
- hit the 'Encrypt' button.
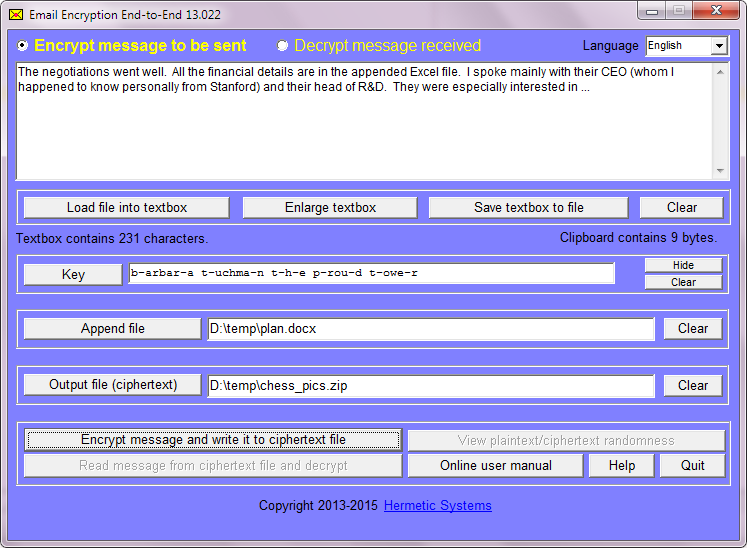
EEE then encrypts your report plus the Excel file, and writes the encrypted data to the ciphertext file.
Now you go online and bring up your usual webmail client. You compose some uninteresting message, such as, "Chess tournament went well; got 2nd prize; here's a 'zip' file containing a few pictures of the other prize winners." You then attach the ciphertext file to the message and send it off to your company.
The person at your company who is meant to receive it then saves the attached ciphertext file someplace, then runs EEE and:
- enters the agreed-upon phrase for the encryption key
- tells EEE where to find the ciphertext file and
- hits the 'Decrypt' button.
EEE then displays your report in the textbox (which can be saved to disk) and asks for the location of a folder in which to write the Excel file. After it does this, the recipient can exit EEE and read both your report and the Excel file.
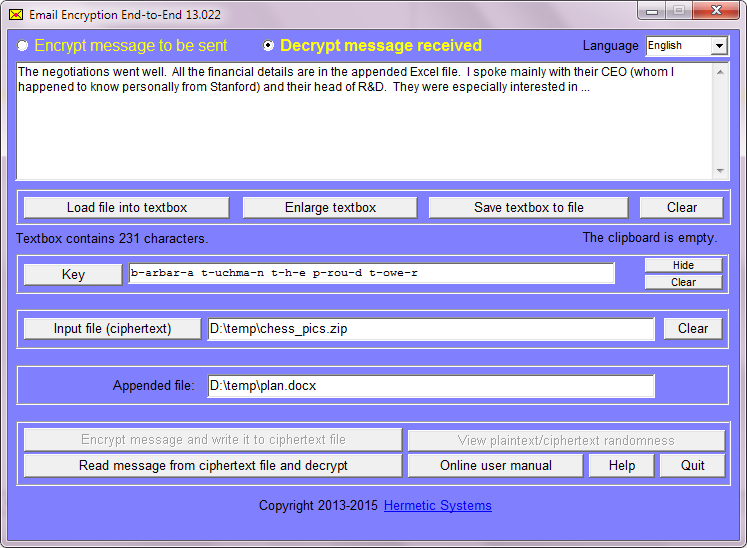
NSA may have sucked up and stored your 'outer' email message in its data bank, but this will appear to be just some message about a chess tournament with an attached 'zip' file referred to in the message as containing images. No UnZip program will be able to unzip it (because it is not a ZIP file), and in fact it can't be read at all, except by someone using EEE and knowing the phrase used to encrypt the data. Your confidential data has been transmitted securely in encrypted form 'end to end'.
Finally, if there is some chance that your laptop might fall into the wrong hands before your return home, you can (after your company has confirmed receipt of your report) delete (or better, securely delete) the ciphertext file which was created by EEE (and perhaps even uninstall the EEE software itself), since the details of your negotiation are now safely in the hands of your company.
| Email Encryption End-to-End Product Page | Home Page |